How Businesses can Protect Themselves
Business email compromise or BEC is when a fraudster either sends an email pretending to be from someone else or infiltrates a business’s email system to send fraudulent emails to trick someone into sending money or revealing sensitive information. As per the Australian Signals Directorate (ASD) Australian Cyber Security Centre (ACSC) Annual Cyber Threat Report 2023-2024, BEC was one of the biggest cyber security threats to Australian businesses in the 2023-2024 financial year. Almost $84 million was lost by businesses through BEC scams – an average of $55,000 per business, which is up from $39,000 the year before.
Case in Point: The Hong Kong CFO deepfake business email compromise scam
With the advancement of technology including Artificial Intelligence or AI, BEC attempts have become very sophisticated. In a recent incident[1] , a Hong Kong-based company fell victim to a deepfake business email compromise scam where fraudsters used AI-generated audio and video to impersonate the company's Chief Financial Officer (CFO) to trick the company’s finance employee into paying out AUD$37million! The elaborate scam saw the finance employee attend a video call with what he thought were several other members of staff, but all of whom were in fact deepfake recreations. This deception led to unauthorised fund transfers, highlighting the advanced methods fraudsters now employ.
Key red flags identified in the scam:
- Unusual Payment Requests – The fake CFO requested large fund transfers under the guise of a confidential business transaction, which was unusual for the company’s corporate policy and procedures.
- Urgency and Confidentiality – The fraudsters pressured employees to act quickly, discouraging them from verifying the request through standard internal controls.
- Uncharacteristic Communication Channels – The fraudsters used a video call to imitate the CFO, deviating from the typical in-person or internal corporate communication methods.
- Inconsistencies in Background and Facial Movements – Employees later reported that the video call had subtle but unnatural facial movements and slight audio delays, which are common indicators of deepfake manipulation.
- Lack of Secondary Confirmation – The employee did not seek secondary verification from another trusted executive or through a different communication channel.
How businesses can protect themselves against these sophisticated fraud attempts
To combat these evolving threats, our recommendation is that organisations must adopt comprehensive fraud and corruption control measures. In Australia, the Australian Standard AS 8001:2021 Fraud and Corruption Control (the “Standard”) is the guiding principle and backbone of guidance on how to prevent, detect, and respond to the risks of fraud and corruption. This Standard provides a comprehensive framework for identifying and mitigating fraud risks, including the integration of cyber fraud risk considerations.
The Standard emphasises the importance of:
- Prevention: Establishing robust internal controls, including segregation of duties when approving and paying invoices, user access controls to prevent unauthorised transactions, and fraud awareness training for employees to recognise fraudulent schemes.
- Detection: Implementing real-time monitoring mechanisms to identify fraudulent activities promptly, such as AI-driven anomaly detection in financial transactions and robust email authentication protocols.
- Response: Developing clear investigative incident response procedures to address and remediate fraud incidents, including designated reporting channels and rapid escalation protocols.
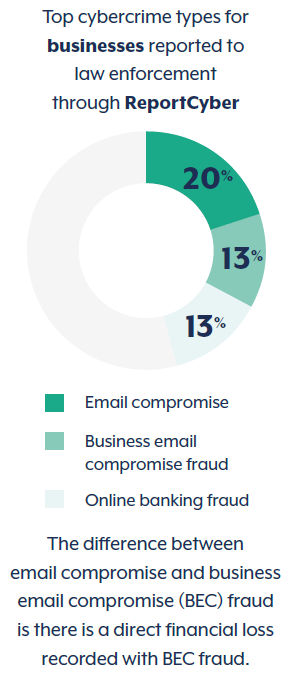 Australian Signals Directorate (ASD) Australian Cyber Security Centre (ACSC) Annual Cyber Threat Report 2023-2024.
Australian Signals Directorate (ASD) Australian Cyber Security Centre (ACSC) Annual Cyber Threat Report 2023-2024. The key components of the Standard to consider include:
- Fraud and Corruption Control System (FCCS): A robust system that replaces traditional fraud control plans, ensuring continuous and dynamic fraud risk management. The FCCS focuses on prevention, early detection, and effective response to fraud and corruption incidents. It involves setting up clear policies and procedures, regular monitoring, and updating the system to adapt to new threats. Organisations must benchmark their FCCS against the Standard to identify gaps and prioritise actions especially against the rise of AI-driven fraud schemes.
- Fraud awareness training: Regular fraud awareness training is essential for all employees, managers, and executives. This training must cover the fundamentals of fraud and corruption, how to identify potential fraud, and the procedures for reporting suspicious activities. By educating staff on the latest fraud tactics and red flags, organisations can foster a culture of vigilance and accountability. Training programs must be customised to the organisation's specific needs and regularly updated to address emerging threats.
- Pressure testing and reviewing internal controls: Reviewing and tightening user access controls is crucial in preventing unauthorised access to sensitive financial systems. This involves implementing role-based access controls to ensure that employees only have access to the information and systems necessary for their job functions. Pressure testing on internal control or conducting regular audits of user access rights can help identify and revoke unnecessary or outdated permissions, reducing the risk of internal fraud. In addition, organisations must review their Segregation of Duties policies especially when it relates to the accounts payable process as it is essential to prevent fraud and errors. This involves dividing critical tasks among different employees so that no single individual has control over the entire process. This division of responsibilities increases accountability and reduces the risk of fraudulent activities.
- Information Security Management System (ISMS): Aligning with the Internal Standard ISO/IEC 27001, this system enhances the organisation's ability to protect against cyber fraud threats. An ISMS is a set of policies, procedures, and controls designed to manage information security risks. It covers all aspects of information security, including physical, technical, organisational, and human factors. Implementing an ISMS helps organisations ensure data confidentiality, integrity, and availability, making them more resilient to cyber fraud attacks.
The integration of AI technology into business email compromise schemes represents a significant fraud threat to organisations. However, by implementing robust fraud control frameworks, such as Australian Standard AS 8001:2021 Fraud and
Corruption Control, and regularly assessing risk exposures, businesses can strengthen their defences and mitigate the impact of these advanced fraudulent activities.

“Australian Signals Directorate (ASD) Australian Cyber Security Centre (ACSC) Annual Cyber Threat Report 2023-2024”.
Your next steps…and we can assist
If you have not recently conducted a fraud & corruption control framework review, now is the perfect opportunity to conduct this review, and we can assist you on this journey. RSM Australia’s Fraud & Forensic Services team as subject matter experts can work with you and conduct an internal audit to assess the design and operating effectiveness and / or the efficiency of processes and controls in place at your organisation related to Fraud and Corruption control; and alignment with relevant regulatory requirements and better practice.
We will provide an independent report to you on the internal audit(s) or review(s) and we can also discuss tailoring a review or suite of reviews to suit your specific needs and that of your organisation.
Remember, prevention is better (always) than remediating the fraud!
FOR MORE INFORMATION
Please do not hesitate to contact RSM Australia Partner Roger Darvall-Stevens, Manager Chris Scott, or any others in RSM’s Fraud & Forensic Services team to discuss how your organisation can enhance its tone at the top and ethical culture or discuss how we can help your organisation with fraud and corruption control better practice.