As the world becomes increasingly digital, there is a need to transfer your business to remain relevant and competitive.
The Information Security is no longer an option. |
Our Information Security services provide security and privacy awareness along with email phishing simulation exercises. Our goal is to safeguard businesses, their customers and staff from the consequences of cyber fraud.
We understand that every business faces unique needs and challenges. Hence, we have the right IT solutions, such as Data Destruction for your business and manage your data safely.
Our Information Security services:
Data Privacy & Security Awareness
We offer data protection and privacy services to help organisations stay up-to-date with leading data security practices and privacy awareness services.
In today’s interconnected world, safeguarding sensitive information is paramount.
Organizations must prioritize data privacy and security to protect their users and maintain trust.
Let’s delve into the importance of these concepts and how awareness services can benefit your organisation.
Why does the Privacy and Security Awareness matter?
Risk Mitigation | Compliance | Empowered Users | Efficient Processes |
Educating employees and stakeholders about data privacy and security reduces the risk of breaches. | Awareness services ensure adherence to legal requirements and industry standards. | Educated users actively participate in protecting their own data. | Awareness leads to better practices, efficient workflows, and fewer security incidents. |
Case Study: Security Awareness in Action
This case study focus on one of the top 10 auditing firm in Malaysia that implemented our data privacy and security awareness service. The firm aimed to strengthen its data security & privacy culture and reduce data breach risks by educating nearly 400 of its employees. We assist and provide guidance to the firm’s Information Security Committee members on the security awareness plan as well as implement new processes. Our team has made improvements to the data collection input processes of the firm. One of the changes made was in the way they recorded visitor information. Previously, all personal data of visitors was written in a book with no proper handling or storage of the book. To ensure better security of personal data, we helped the firm implemented the Visitor Management System (VMS). | 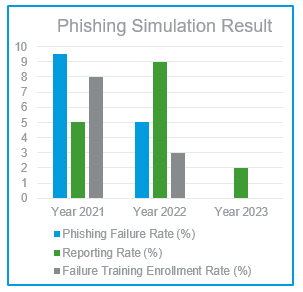 |
We also provide annual Security Awareness Training for all employees and as well for new employees are updated on the latest security awareness topics, such as QR Phishing (Quishing). It is mandatory for every new employee to undergo data privacy and data security awareness training. The quiz has been set up for each course to ensure that all employees have a good understanding of the data privacy and security awareness training. According to the results, there has been a significant improvement in the awareness of data privacy and data security among the employees of the firm. The security awareness failure rate for employees has decreased from 10% to 0% in the past two years. Additionally, there is no tendency for users to click on suspicious phishing email attachments, and most employees have started complying with the firm's information security policies. | |
Our services
- We provide data privacy PDPA Awareness and consultancy services
- Understanding the environment, establishing SOP & committee members and awareness training.
- We provide data security awareness in according to ISO/IEC 27001
- Identify the scope and provide awareness training all users.
What is Data Sanitisation?
Data sanitisation is the process of completely and irreversibly removing data from computing equipment. This ensures that unauthorized users cannot recover information from disposed devices, and it is critical for maintaining data security and privacy.
Our Commitment
We are committed to ensuring that all hardware decommissioning procedures adhere to internal compliance standards. Our secure and professional data sanitisation process ensures that your sensitive information is handled with the utmost care. Whether it's during employee exit procedures or the end-of-life disposal of equipment, we ensure thorough data sanitisation to prevent potential data breaches.
How We Achieve Secure Data Sanitisation…
We employ cutting-edge techniques to guarantee that your data is securely sanitised, leaving no trace of sensitive information. This process involves:
- Using the Certus Secure Data Sanitisation Solution: Our data sanitisation services are powered by CertusSoftware, a leading solution in secure data sanitisation.
- Comprehensive Infrastructure: Our solution is equipped with a robust infrastructure that guarantees the secure and compliant sanitisation of sensitive data.
- Erasure Certificates: Upon each successful data sanitisation process, the solution generates an erasure certificate with a unique digital signature as a seal of authenticity. This certificate confirms that the data has been successfully and permanently sanitised, ensuring compliance with regulatory and legal obligations.
When is Data Sanitisation Necessary?
Data sanitisation is crucial in the following scenarios:
- Employee Offboarding:
When employees leave the company and need to return their IT equipment, ensuring that all data is securely sanitised prevents unauthorized access and maintains the integrity of your company's information.
- Disposal of old and end-of-life equipment:
Before old equipment leaves the organization's control, it is essential to ensure that all data is completely and securely erased to prevent data breaches.
How can we help?
Our data sanitisation services cover a wide range of business needs, including:
- End-of-life Equipment Disposal: Ensuring old equipment is dispose off securely.
- Employee Exit Procedures: Sanitising data from returned IT equipment when employees leave the company.
- Regulatory Compliance: Assisting in ensuring compliance with data protection regulations by securely erasing sensitive information.
- Versatile Device Support: With our Data Sanitisation Solution, you can sanitise data on PCs and laptops, servers and storage devices, loose drives and mobile devices (tablets and smartphones).
- EaaS (Erasure-as-a-Service): All our services are conducted by Certified Data
- Erasure Engineers trained by Certus Software to ensure data integrity and compliance with standards such as NIST 800.88r1, GDPR, SOX, HIPAA, IEEE, and others.
Compliant with
The GDPR law requires that the user must have the ability to have personal data erased and receive written proof of this. The right to erasure is also known as ‘the right to be forgotten’.
The NIST SP 800-88 Guidelines for Media Sanitization provide instructions to organizations on how to effectively erase storage and mobile devices in a secure and permanent way.
In today’s digital landscape, cyber threats are ever-evolving, and organizations must stay vigilant to protect their sensitive information. One effective approach is conducting phishing simulations to educate employees about the dangers of phishing attacks.
What do news stories in common?
- Human Error
- Phishing Scam are Everywhere
- We are easily fooled
Email Phishing Simulation
Simulate real email phishing attacks and deliver trainings.
Simulate Phishing Attacks & Training
Social engineering attacks are becoming increasingly common in today's environment, and the weakest link in a company's security defence is often the human element. As part of a comprehensive approach to human risk management, we offer simulated phishing attacks to test employees' security awareness.
Our email phishing simulation enables you to create custom groups with as many phishing targets as necessary and sync your target database via our API and webhook integrations.
We provide personalized training to assist employees in improving their security awareness.
We believe that by investing in the training and development of our employees, we can create a safer and more secure work environment for everyone.
Our service
We offer an email phishing simulation platform for every business needs.
Realistic Templates
| Readily made library impersonating trusted brands. |
|---|---|
In-Depth Reporting
| Analyze the performance of users, departments |
Monitoring
| Monitor the user risk level |
Follow-up Training
| Educate compromised users and provide training. |
Improve your organization's security posture by conducting an email phishing simulation service with us!







