Overview
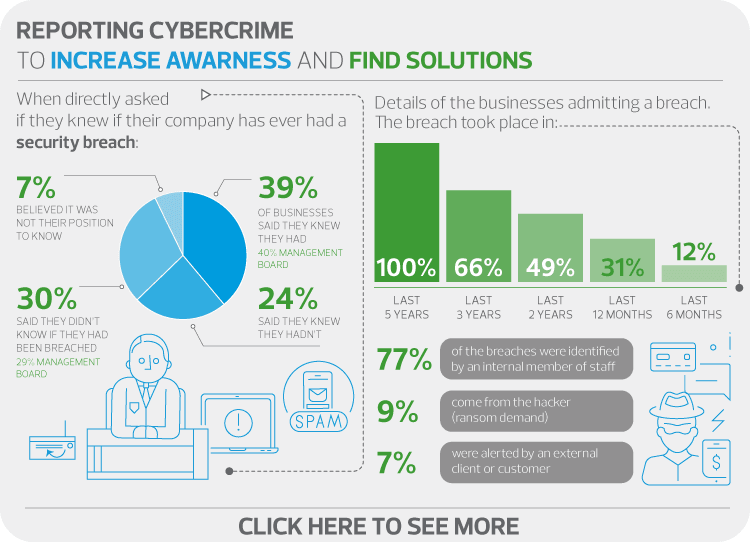
A significant number of companies in RSM's survey on cybersecurity admitted a security breach and gave details about how they had dealt with it and its impact. The findings confirm the critical role of the employee with most attacks identified by them and/or access gained through them. Positive direct action after the event is seen with investment in software, training and much needed IT security reviews. However, one key issue highlighted is the lack of transparency of the breach with 75% of breaches not becoming public knowledge.
"Tell it all, tell it fast, tell the truth"
Key findings
Insights from RSM
Firstly, the data highlights the importance of the role of the employee and the need for cybersecurity training throughout organisations. The greatest risk within an organisation comes from the inside as most breaches come via employees. Therefore, internal morale in a business takes the biggest hit after a breach. Having a culture which encourages staff to report data breaches is key to ensuring that the real scale of the threat can be determined, and importantly, so that root cause analysis can be undertaken to help prevent future attacks.
We also see a confirmation of ‘action after the event’ with the majority of firms investing in software and training in the long-term. However, given the volume of ongoing cyberattacks, the findings also ring some alarm bells. Only 27% of businesses searched for and found further vulnerabilities in defences post-breach, and only 26% developed or updated crisis planning to include security. That leaves the majority of organisations in the same place they were before the breach occurred.
Worryingly, only 15% of businesses reviewed third-party suppliers. As businesses are increasingly reliant on third-party service providers, it is vital to ensure that these third-parties have effective security, controls and processes in place to maintain the security and resilience of their operations. Independently assessing third-party operations can give senior executives and the board the assurance required over these outsourced providers.
When we address the finding that in 75% of the businesses, the breach did not become public knowledge, there is one key question - did it need to? Arguably, yes. If firms are keeping breaches under the radar (for fear of financial or reputational damage for example) then we have a harder task of making businesses understand the risks. If you are continually told something will happen but don’t see evidence of it, you will be less likely to believe it or be inclined to take action against it. If those 75% talked about the issues and problems, there would be movement in the market, more awareness at CEO level, increased software solutions and better protected organisations. Reporting breaches would be a great help to the industry.
However, there is a balance to be found when it comes to reporting a breach. There are factors to be considered: what is the regulatory requirement? Is the data that was breached personal information that could cause distress to an individual? Has a high volume of data been breached? If not, do we actually need to know? Most businesses will be subject to a large number of attempted attacks, but they may not result in significant damage.
What the regulator is required to know causes much confusion. 34% of businesses have admitted they do not fully understand in what circumstances, or in which level of breach, the regulator should be informed. Clarity is needed. At the moment this will only take place as more breaches and fines occur.
Overall, we need to see a broader reporting requirement across every industry. Not only would increased transparency drive greater protection but the fact that there are businesses outside of regulation that don’t need to report anything at all shows a lack of balance.
We would advise a sensible approach while understanding the duty of care and governance requirement to all stakeholders.
Gregor Strobl Sheila Pancholi
RSM Germany RSM UK